LIBRARY NETWORKS
2.1 LIBRARY NETWORKS : MEANING, NEED & OBJECTIVES
2.1.1 Meaning
2.1.2 Need for Networking
2.1.3 Aims and Objectives of Library Networks
2.2 FUNCTIONS OF LIBRARY NETWORKS
2.4 NETWORK TECHNOLOGY: A BRIEF IDEA
2.4.1 Basic Network Architecture/Topology
2.4.2 Hardware Components of a Network
2.4.3 Types of Networks
2.4.4 Network Protocols and Standards
2.4.5 CD-ROMs
2.5 ESSENTIALS & REQUIREMENTS FOR LIBRARY NETWORKING
2.5.1 Hardware and Software Requirements
2.1 LIBRARY NETWORKS : MEANING, NEED & OBJECTIVES
2.1.1 Meaning
The development of sophisticated technologies in computer and communication field has upset libraries world wide in storing and transmitting information. The computer and its communication circuits link to other computer or to terminals constituting an integral information machine. This technology introduced the `Network System’. When a group of libraries using computers decide to exchange information, a network is developed. The National Commission on Libraries and Information Science (NCLIS) in its National Programme Document (1975) defines a network as:
"Two or more libraries and/or other organizations engaged in a common pattern of information exchange, through communications, for some functional purpose. A network usually consists of a formal arrangement whereby materials, information and services provided by a variety of libraries and other organizations are available to all potential users. Libraries may be in different jurisdictions but agree to serve one another on the same basis as each serves its own constituents. Computer and telecommunications may be among the tools used for facilitating communication among them".
According to Martin:
"A network is a group of individuals or organizations that are interconnected. The linking must include a communication mechanism, and many network exist for he express purpose of facilitating certain types of communication among their members. In the library world, institutions from network primarily to achieve better sharing of resources – resources consisting of bibliographic information and of collection – and better services to patrons". It must be emphasized that the particular focus in this gathering will be on online networks, those using computers and linking members to the computer resources by means of telecommunication connections.
A library network is a description of an activity which existed before the term itself was devised. When any two libraries talk to each other, we have the fundamental condition for networking, that is exchange. When one library provides a service to another, we have the rudiments of network behavior. Inter-library loan or bibliographic exchange in any form, is the chief justification of a network.
Networking is a system with a predominant How of service and a reverse flow of demand. When a librarian asks his neighbour for a book or a citation and his request is honoured networking begins. Librarians now tend to view a collection as not merely what they possess in their institution, but all materials they have access to through photocopying, inter-library loan and reciprocal borrowing privileges.
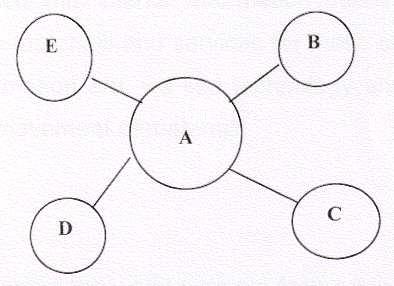
A typical network (though various models) looks like

Where A, B, C, D, E are participating libraries, the central node (A) has the responsibility of maintaining and operating the centralized databases. In such environments, the participating libraries have the obligations to contribute all the bibliographical data pertaining to their respective collection to the central node. The libraries may be linked through telephone lines or through satellite depending upon the situation. In whatever way, they are connected the most important issues in such a network are related to creation, maintenance, and operation of centralized databases.
So on the basis of above explanations, we notice that library networks have the following characteristics:
Data : Bibliographic records (MARC) frequently
Retrieval : Author/title/number (subject) (keyword)
Access : Telecommunication network/Private network/Hard wired network
Users : Librarians (Public)
The above classification shows that library networks have the following features:
Networks enable librarians, faced with clients’ information needs beyond their local resources, to identify and obtain materials and services for those clients. As we move increasingly into electronic information era, we see technology and networks working together to reduce the physical movement of materials.
2.1.2 Need for Networking
As a universal phenomenon, libraries the world over are facing two major problems. These are:
The number of publications in various disciplines, especially in Science and Technology is alarming. It is estimated in the past that the primary source of literature in the field of Science and Technology is doubling in every 15 years whereas it now doubling in 10 years. According to UNESCO statistics of World Book Production, about three lakh books are published every year. The number of learned journals in the field of science and technology alone has now come to the tune of 60,000 adding at the rate of 1000 journals a year approximately.
Another important problem the librarians/information professionals are facing is the constant increase in the prices of library documents. Since Indian libraries have to depend mainly on foreign publications, especially in the case of science and technology journals they have to face sharp increase in the rates of subscription and downward changes in the value of rupees. This hydro-headed problems have forced the librarians and information specialists to cut down the number of journals they procured to manage the situation within the available resources.
Another problem is increasing cost of library services as costs of library services have skyrocketed, libraries have realized that through cooperative arrangement there is the possibility of providing new services whose cost would be spread over many institutions. The concept of cooperation proves much effective and satisfies the user needs in a better way.
Thus, we notice in order to find a solution to the problems faced by libraries/information centers regarding information explosion and costs, library networks have been established for cooperation and resource sharing among libraries so that one individual libraries may not feel burdensome while handling vast amount of information and price escalation of library documents and services.
2.1.3 Aims and Objectives of Library Networks
As we have seen earlier, the basic purpose for creating a network is to provide information services to member libraries through sharing of resources of the participating libraries of the network. This may lead to member libraries to depend more on access to documents held in the other member libraries than on depending only on their respective collection. The main aims and objectives of library network are stated as the following:
( i ) To promote resource sharing and co-operation activities among libraries by providing efficient and reliable means of resource sharing, e.g.(ii) To improve resource utilization and service level at the individual libraries by providing automation facilities in the following areas:
(iii) To coordinate efforts for suitable collection development and reduce unnecessary duplication wherever possible. The purpose is
(iv) To establish referral centres to monitor and facilitate catalogue search and maintain a central on-line union catalogue of books, serials and non-book materials of all the participating libraries.
(v) To develop a specialist bibliographic database of books, serials and non-book materials for search and access.
(vi) To create a database of projects, specialists and institutions for providing online information services.
(vii) To coordinate with other regional, national and international networks for exchange of information and documents for the use of libraries and users.
(viii) To evolve standards and uniform guidelines in techniques, methods, procedures, hardware and software, services and so on and promote adoption in actual practice by all libraries, in order to facilitate pooling, sharing and exchanging resources and facilities towards optimization.
2.2 FUNCTIONS OF LIBRARY NETWORKS
Library Networks have been established with the main purpose of sharing resources so that unnecessary wastage of limited finance with them can be avoided. However, not all networks conform to the essential functions of library networks. It is noted that the essential functions should include the promotion of resource sharing, creation of resource sharing tools like union catalogues, rationalization of acquisitions and adoption of international standards for creation of records uniformly and delivery of documents. Keeping these things in view, functions of a typical library network might fall into the following three categories:
(i) Information services to users
(ii) Technical services to member libraries
(iii) Management service to the network administration
Information and technical services are goal-oriented, i.e. to fulfill the primary goal of the network. Functions that serve the users directly, i.e. information services to users are:
Information services
Technical Services
Functions that serve the libraries i.e. the technical services are:
Management services
The management services, i.e. functions that support the network administration are:
- collection of statistics
- analysis of performance of the network
- user studies
staff development programmes
user oriented programmes
It involves
- determination of costs, fees to be collected, etc.
- allocation of budgets
- holding of meetings
- publication of newsletters, etc.
The earlier stated functions of a network can be implemented in different models of networks.
The structure of a network will depend upon the purpose for which libraries use it. A number of libraries should join the network that offers the facilities to make their functioning simpler, better and more cost effective. For instance, university libraries in a state may choose a model which is of totally decentralized type. However, the affiliated colleges in a university system can be linked to the respective university library, such a model may be known as distributed type. The public library system may choose a model of hierarchical type. Special libraries in a city may choose a model, which is of totally decentralized.
These are three basic anatomical structures, namely:
- Star network
- Hierarchical network
- Distributed network
Star Network
In a star network, one of the members maintains and operates a centralized bibliographical database. This database consists of all the bibliographical records of every member libraries. The configuration may be
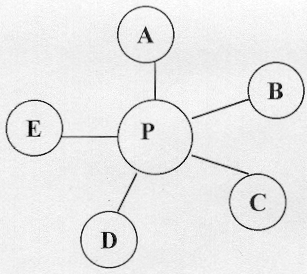
The node P holds all the bibliographical resources (databases) with all other members A, B, C, D, E utilizing these resources. It is the obligation of the node P to maintain and update the databases.
Hierarchical Network
Each member shares resources locally; each participating library at the lower level passes unsatisfied needs to the participating library which is at the higher level. The requests remaining unsatisfied are referred to the `library of last resort’ which may be obliged to check other centres to locate required materials. The configuration is:
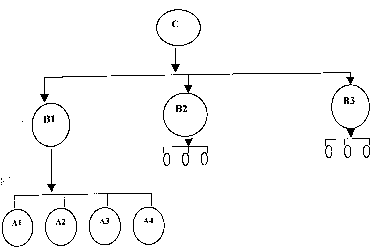
Users of the network, members A1, A2, A3, A4 are mostly satisfied with the resources available in their respective libraries. Unsatisfied requests are passed on to the higher level resource centre B, finally the few remaining unsatisfied requests are referred to the library of last resort C which may be obliged to check other centres B2 and B3 to locate required materials.
Distributed Network
In a totally decentralized model, a type of distributed model, all network members hold in theory different resources which they may share with one another.
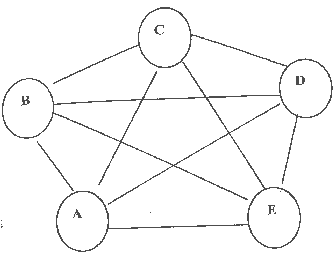
Here all members A, B, C, D, E, have different resources which they share with one another.
A modified model of a decentralized network looks like
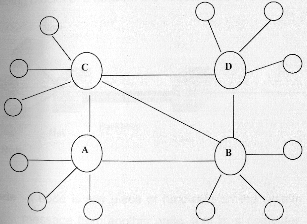
Here A, B, C and D are themselves a network, either to star type or a hierarchical type.
2.4 NETWORK TECHNOLOGY: A BRIEF IDEA
The world over, library networks and consortia have developed technologies to facilitate the process of accessing databases, retrieval of information, processing of interlibrary loan requests and the delivery of documents. So we must have some idea about the network technology in general – various terms used in the context of networking, standards, protocols and the software that convert data from one format to another and the technology relevant to Information and information Service field in particular.
2.4.1 Basic Network Architecture/Topology Top
A network’s architecture is the way the data flows within the network. The basic building blocks of a network are nodes, hubs and backbones

-a node is any piece of hardware on the system that can be addressed by a message from another node, that is, a computer, printer, fax, modems or CD-ROM drive.Node
Hub -It is a device that accepts multiple connections. Nodes are connected to it. It, also known as concentrator, simplifies the wiring of the nodes to each other and routes signals between the nodes. There are many different types of hubs. Some are simple hardware devices that only accept connections called passive hubs; others are complicated electrical components that monitor and control the flow of information to various network locations called active hubs.
Ring Architecture
It arranges the nodes on the network in a circle. When one of the computers on the network sends a signal, it passes it to the next node on the network. If it is not addressed to that node, it is retransmitted to the next node and so on around the circle until it reaches the node it is addressed to. The connections between computers are not direct, instead, each computer attaches to a hub and the ring itself resides inside the hub.
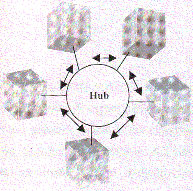
Star Architecture
It has the nodes connected to a central, host, computer when one of the computers as the network sends a signal, the next routes it to the node it’s addressed to. There are no direct connections between the nodes on the network except through the host computer.

Bus Architecture
Bus, or linear, architecture connects all nodes to a single bus much as the components are organized within the computer. A signal addressed to another node is sent to the bus. All other nodes on the network examine the signal to see if it is addressed to one of them. Typically, wires connect each node to the network’s backbone, which is a fixed length of cable with terminator at both ends to stop reflections when signals hit the end.

2.4.2 Hardware Components of a Network
(i) Servers
A server on a network is any computer that can shared by other computers working on the network. In many cases, the server has to be the most powerful computer on the network, because it is shared among so many users or clients. These clients (computers) depend on the server for programs and data, or connection to other computers and devices.
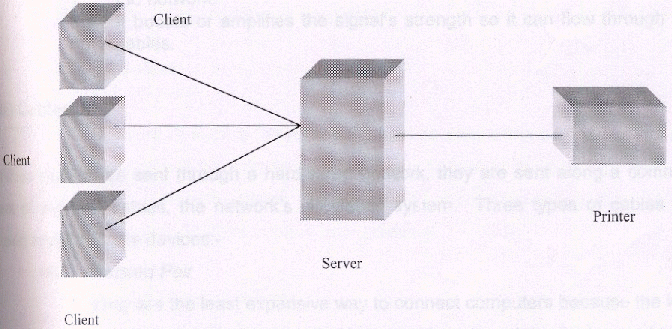
File Server
It stores data files and some application programs. It has large amounts of secondary storage in the form of hard disks, CD-ROM drives, tape drives and other storage dievices.
Print Server
It stores print jobs on a hard disk until the printer is ready to handle them.
Communication Server
It can be a fax or modem over which data from any other node can be sent. It can also be used as a gateway to the Internet.
(ii) Network Interface Card
It is the key component of the network workstation. It serves a number of purposes:
- It makes the physical connection or bridge between the computer and the network.
- It converts the parallel data on the computer’s bus into serial data for the network.
- It boosts or amplifies the signal’s strength so it can flow through the cables.
(iii) Cables
When signals are sent through a hard-wired network, they are sent along a common set of wires or cables, the network’s circulation system. Three types of cables are used to connect the devices:-
(a) Twisted Pair
They are the least expensive way to connect computers because the wire is cheap and easy to install. However, they are relatively slow and have a tendency to pack up noise that can cause high error rates.
(b) Coaxial
It is the most common type of networking cable. It consists of an inner wire surrounded by a layer of insulating material that is, in turn, surrounded by a braided wire. They are more reliable and durable.
(c) Fiber-optic
It connects of the glass or plastic filament, protector by thick plastic padding and an external plastic sheets. It uses a pulse of laser light instead of an electronic frequency to transmit a signal. Fibre optic cables are fast and reliable, as well as small and light. They have an extremely wide bandwidth, so a large number of signals can be sent simultaneously.
Baseband Cable:
A cable that transmits only one signal is called a baseband cable.
Broadband cable:
This can handle simultaneous transmission of different signals by sending them at different frequencies. Broadband cables are more expensive and require additional frequency modulating equipment.
(iv) Network Devices
When signals are sent through a network, they must be sent in the right direction, and they must also sometimes be amplified so they travel farther or converted so they can be transferred to a different network. These are the roles of a series of hardware devices called repeaters, bridges, routers and gateways.
2.4.3 Types of Networks(a) Repeaters (or Physical relays)
They connect segments of a network, and since signals get weaker and less distinct with distance, these small devices refresh and enhance them before sending them along. They are usually used to extend the network in effect joining two networks together by passing a cable signal between them.
(b) Bridges (or Data Link Relays)
They connect networks, which use different physical links. For example, a network running on twisted pair wires is connected to one using coaxial cable with a bridge.
(c) Routers
They control where messages are sent on networks. The router keeps the addresses of other nodes in a table. If the address of a message sent through the router is on the network, the message is forwarded. If the address is not on the network, the router towards the message to another network by sending it to a gateway.
(d) Gateways
Gateways are used to connect different types of networks. Since two networks may not share a common protocol, these devices translate each network’s protocol so the other network can understand the data.
(i) Client Server Based Networks
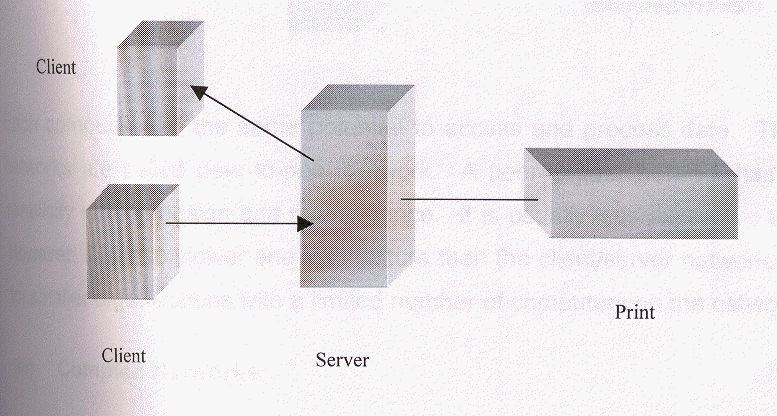
In this system, clients are usually computers on the network that are operated by human beings, making changes to the data files they receive and when these changes are complete, sending the data back to the file serve for storage.
This arrangement has the virtue of processing efficiently, especially on large networks with dozens or even hundreds of machines. With the full processing power of a very powerful computer allocated solely to sending and sorting files, individual clients are not kept waiting for data and they can process different files with different software independently of each other.
The only disadvantage with this kind of network is that if file server goes down, the whole network comes to a halt.
(ii) Peer-to-Peer Network
Each computer has the same potential to access and process data. These types of networks are called peer-to-peer network. A peer-to-peer network has the virtue of simplicity in both design and maintenance. It is usually less expensive to set as well. However, it is also slower and less secure than the client/server network. It is suitable for smaller organizations with a limited number of computers on the network.
(iii) Complex Networks
A network can be connected to other networks and networks can consist of different types of machines from different vendors each with its own unique way of handling electronic information, not directly understood by other machines on the network. Special software and hardware can be attached to the network to handle this complicated set up. These devices are called bridges, routes and gateways, perform in different ways the task of "translating" the electronic information supplied byt one machine into a format that can be understood by another.
(iv) LAN, MAN, WAN
These networks are classified according to their geographical coverage
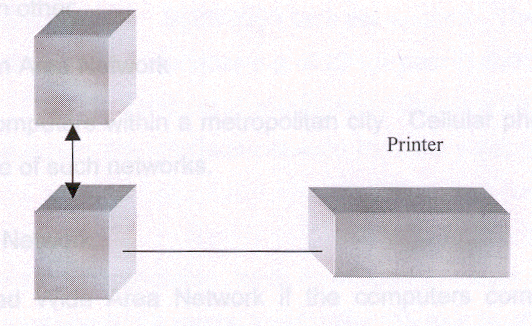
Local Area Network(a) LAN –
A network is called Local Area Network if the computers comprising it are located within the same building or within a distance range less than one kilometer from each other.
(b) MAN – Metropolitan Area Network
It inter-connects computers within a metropolitan city. Cellular phone networks are a good example of such networks.
(c) WAN – Wide Area Network
A network is called Wide Area Network if the computers comprising it are distributed over a large geographical region may be all over the country, all over the world or any distance range more than 30 kilometer. Parts of the network may be connected by the cables and other parts by microwave or satellite transmission. Typical wide area networks are those operated by the telephone companies. The Internet is probably the widest of all networks in that it links not only LANs but also other WANS.
2.4.4 Network Protocols and Standards
If computers are to talk to each other, they need an agreed set of rules called protocols by which they can communicate. The protocols are techniques to govern the flow of data from one computer to another. For different types of computer to be able to communicate effectively, standards need to have been set for the periodicals.
(A) Network Standards
These standards may result from international agreement or do facts, from a particular manufacturer becoming dominant in the networking field. The three most important bodies involved in setting standards in the field of computer networking are CCITT, ISO and IEEE.
CCITT (Comite Consultatif International Telegraphique et Telephonique) International Consultative Committee for Telegraphy and Telephony, are responsible for the V, X and I standards. The V standards are for data communication over in Public Switched Telephone Network (PZSTN), e.g. the modem standards V21, V22 of 300/300, 1200/1200, 2900/2900, 1200/75 and 9600/9600 bets per second. The X standards are for dedicated data communication services e.g. X.25 for packet switching services and X.400 for messaging. The I standards are for Integrated Services Digital Networks (ISDN)) e.g. I.400 series specifies the interface between the user equipments and the network.
ISO, the International Standard Organization, have developed a 7 layer model known as Open Systems Interconnection (OSI) model to describe the way in which computer networks operate. This model ranges through from the physical connections at level 1 through the transport protocols at level 4 to end-user applications at level 7. The purpose of this model is to help develop `open’ standards.
IEEE, the Institute of Electrical and Electronics Engineers, an American body, have developed and recommended standards for the physical connection of computers. In the networking field, since 1985 they have developed standard 802.5 for Token Ring Networks and 802.3 for an Ethernet connection between computers. These standards have been adopted by ANSI (American National Standards Institute) and ISO.
(B) Protocols controlling data transfer over the network
In the early 1960s when researchers tried to connect computers with each other, they thought of various techniques to govern the flow of data from one computer to another. Some of them are:
(i) Netware Core Protocol (NCP)
Developed by Novell Netware, it manages the flow of data between Netware Clients and File Server for maximum efficiency. It is earliest of the protocol among different Network protocol to govern the flow of data from one computer to another. It is a combination of Bits with different portions representing functions to be performed.
(ii) Transmission Control Protocol/Internet Protocol (TCP/IP)
TCP/IP works on the principle of packet switching which involves breaking the data into small chunks and sending these chunks along the network. TCP devides the data into small chunks with each chunk not exceeding 546 bytes and pass them to IP, the next protocol in the transmission process. Each pocket is attached with information about source and destination; this resulted into many packets flowing through the same network line with each data pockets reaching its correct destination.
(iii) Internet work Packet Exchange (IPX)
It handles data verification and addressing responsibilities for flow of data between different networks, e.g. between Netware Networks and other networks. It adds a header to the information received from TCP Protocol containing the address of the destination, then it passes the data to Network Interface Card for transmission.
(iv) Sequenced Packet Exchange (SPX)
It verifies the accuracy of the data by using Network Operating System (NOS). It also verifies the accuracy of the remote station to which the data is to be sent by performing some initial communications with the destination workstation. If it gets a confirmation back from the remote or destination station only then, it sends out the data, otherwise it reconfirms by sending the repeated communications. If it fails to get a response from the destination, it issues a notification to the application programme about the failure of the data transmission.
(C) Standards & Protocols : Library and Information Science Field
Resource sharing technology cannot work effectively unless appropriate tools are developed. These tools include the creation of standard bibliographic databases such as union catalogue of books and periodicals, union lists of serials, bibliographic databases of articles and other types of materials, such as CDs, Video-recordings, Sound recordings, theses and dissertations. It becomes necessary to use the methods and tools that help in quick and identification and deliver of documents. However, the adoption of different bibliographic standards creates incompatibility problems and that acts as a major barrier in the use of bibliographic and related information. The standards, protocols and the software that convert data from one format to another should be of international standard.
(i) Bibliographic Standards
Format compatibilities are necessary for computerized catalogue data and these are being standardized by the International Standards Organization. ISO 2709 has been adopted the world over and the efforts to harmonize MARC formats are on. The Library of Congress and National Library of Canada achieved the result in harmonizing their MARC formats in 1997. It is hoped that various MARC formats will also get harmonized in due course.
Maintenance of bibliographic standards uniformly is essential for quick exchange of records, e.g. Delhi Library Network (DELNET) has adopted the following standards:
Standards have been developed by the International Standards Organization and National Information Standards Organization of the US besides a number of national standards organization for creating standard bibliographic and information products. Some examples are as following:
National Information Standards Series : ISSN 1041-5653
z39.2-1994 - Information Interchange Format
z39.901992 - International Standard Serial Numbering
z39.14-1997 - Guidelines for Abstracts
z39.14-1993 - Guidelines for the Construction, Format and Industry
z39.44-1486 - Serials Holding Statements
The other standards include:
Information Retrieval
(ii) Communication Standards
The effective electronic resource sharing has been hampered by the inability to interconnect, effectively and economically, many diverse electronic library and information databases, which exist worldwide. These standards provide the mechanisms to reduce the existing fragmentation of information and service delivery.
z39.50
z39.50 (ANSI/NISO z39.50-1995 (ISO 23950)) is an American National Standard for Information Retrieval Prepared by the National Information Standards Organization (NISO), it defines how one system can cooperate with other systems for the purpose of searching databases and receiving records. As a network protocol, the z39.50 standard provides a set of rules that govern the formats and procedures for the exchange of messages between a client and server, enabling the user to search remote databases, identify records which meet specified criteria and to retrieve some or all the identified records. It is concerned, in particular, with the search and retrieval of information in databases. It simplifies the search process and enables uniform access to a large number of diverse and heterogeneous information sources.
In library networking, z39.50 has assumed greater importance and is the most important protocol available today. In sum, this protocol:
- Provides a mechanism, using clients server model for transmitting and managing queries and result sets
- Is a generalized mechanism and can be used for bibliographic, full text and other types of databases
- Enables the client to perform searches and creates result sets. The records pertaining to the results can be presented to the client or used for creating new result sets with other searches
- Conforms to one or more common syntaxes and yet it is not necessary that he same syntax is shared in all databases.
The methodology for interaction between a client and server is as follows:
1. A client sends an INITIALISE request and server responds with INITIALISE response.
2. As soon as the session is established, the search request can be made by the client.
3. The server respects with the search results
4. Only one search result is made at one time and is served.
5. Records are transmitted to the clients as soon as the client makes the PRESENT request.
There are other facilities like account control, deletion, termination of the session and enhanced features like sort, browse, ILL, etc.
For libraries, z39.50 could very well provide a single interface allowing libraries to support a number of different services. Various library applications include
In India, Indian Agricultural Research Institute, Pusa Road, New Delhi has taken the lead to install the first z39.50 server in India and make to databases available to the z39.50 clients.
ILL Protocol
The ILL protocol is used to provide just ILL services. Several vendors use it in their software. In the ILL protocol, the services represent the activities. These services are such as ILL request, RECEIVED, RETURNED, RENEW, LOST (item requested is lost) and CANCELLED (cancellation of the request). There are optional messages such as SHIPPED, RETURNED, RECEIVED and CHECKED-IN. When the requests are in operation, the messages such as PENDING and IN-PROCESS are used. These are several other services used by the protocol and they are requested by messages such as ILL-ANSWER, FORWARD-NOTIFICATION, etc.
The National Library of Canada has developed a protocol for ILL communications in order to facilitate resource sharing in a networking environment. The protocol has been designed to encourage software developers and members of the library and the information community to adopt the protocol and incorporate it into ILL systems. The protocol is expected to be POST (Open System Interconnection) based and is able to communicate with all types of hardware, software communication facilities used. OSI provides interconnectivity and interoperability in order to communicate with all types of hardware and allow transfer and communication of data among them. Improvement of interlibrary loan facility through electronic messaging is possible if we use Open System Interconnection (OSI) Reference Model and improve the telecommunication infrastructure.
2.4.5 CD-ROMs
The CD-ROMs technology influenced its wider applications in libraries since 1980s as a major resource of information, which can be used for
For example, a CD-ROM union catalogue can offer an offline access to the resources of a library network which is both convenient and inexpensive. When an online system fails in a participating library, the use of CD-ROM could be proved very useful. Besides, information stored on CD-ROM attached to one of the computers on the network, can be accessed by users on another computer on the network. This is known as CD-ROM networking.
Initially, CD-ROM was distributed on a single workstation configuration, which was too expensive for the small institutes and information centers. However, introduction of multi-user and multi-disk CD-ROM system have made cost and sharing of information more economical for most of the organizations, especially where the same data or database are required for several users.
2.5 ESSENTIALS & REQUIREMENTS FOR LIBRARY NETWORKING
Since Library Networking is meant to promote and facilitate sharing of resources available within a group of participating libraries, several factors are to be considered for planning such on a network. The following are very important:
(i) Member libraries must justify need for a network. The development of a viable network demands planning not only among the network members but also between the members and users themselves.
(ii) Member libraries must agree upon a network policy is to be implemented. The policy must clearly state:
(a) Objectives of the Network- e.g the main objective may be to share the resources among the member libraries. It may be achieved in several ways, for example,
(b) Network Structure
Member libraries should adopt that structure of a network, which will fulfill the purpose for which libraries use it. The lack of arrangement in developing a network structure undermines both the approach of functions and planning.
(iii) Member libraries must identify the funding agencies and mobilize the resources in advance. The financial resources must freely flow while implementing the system. If necessary, network fee may be collected from each of the member libraries. The examples of library networks in the western countries suggest that all networks based on a fee structure can be maintained without grant and are viable in the long run.
(iv) For resource sharing among member libraries, it is necessary to create bibliographic tools like union catalogues and union lists based on the resources available in the participating libraries.
Depending on the objectives or type of network model, databases of library collections should be developed. If the network is of star type, a centralized database consisting of all the records in all member libraries is necessary. If the network is of any other type, database for each of the library collections has to be developed separately.
(v) For the purpose of creating databases, it is essential to agree upon a standard. All libraries should follow a standard MARC format, AACR-II, a standard thesaurus like Library of Congress Subject Headings (LCSH) etc. uniformly.
(vi) Although efforts should be made to have one classification scheme in all participating libraries but use of different numbers should not become a hurdle as search requests are mostly by authors, titles, editors and subject descriptions.
(vii) Member libraries must agree upon indexing system to be followed. In a centralized database system (a star network), it is preferable to adopt a single systems of indexing, i.e. POPSI, chain indexing or any other system. However, in a decentralized or in a hierarchical system, each library may have a freedom to adopt an indexing system of their choice. In such cases, the software must be developed to switch from one database to another database and then one indexing file to another indexing file while searching.
(viii) For the success of network in a long run, each of the member libraries must have a policy to automate every function of the library – acquisition, cataloguing, classification, serials control, circulation, SDI, current awareness services etc. – in the shortest possible time. This helps the library to have computer culture which is required to design, develop, maintain and to operate several databases, to reduce the cost of library operations as well as network operations.
(ix) The major problem in each of the member libraries when attempts are made to prepare the machine-readable records for the existing catalogue. Prior to creating such records, one has to identify frequently used and infrequently used documents. Then prepare the machine-readable catalogue appropriately for the frequently used documents or alternatively use the existing machine-readable databases by down-loading from CD-ROMs or from other databases and reformatting them, one can select the appropriate records for their respective database.
(x) The network should be able to recommend to participating libraries the type of hardware and software they need for their in-house functions and for networking purposes. Hardware should be selected considering the number of entries the participating libraries can generate within the next 3-5 years. The hardware at the Central Host speed with which participating libraries generate records and the network pools them into the Central Hose.
The network software may or may not support the in-house operations of the libraries in the beginning but eventually the network software should not only be able to create union catalogues or full text databases, etc. but also get integrated with the in-house operations.
(xi) If there is no adequate trained manpower in each of the member libraries, attempts should be made to train or/and recruit library personnel.
(xii) In addition to the databases, hardware, software and trained manpower, it is preferable to have certain communication facilities such as Fax, Telex, Telephone, etc. as a part of the network system in each of the member libraries for the effective working of the network. E-mail and INTERNET facilities should be available with the libraries and they should be able to access international databases, preferably individually or through the network host to begin with.
(xiii) Inter-libraries loan services should grow and may be interlinked with the search of the union catalogues. Delivery of documents should be fast, either electronically through fax or through courier or Mail. Rationalization of acquisitions needs to be undertaken.
(xiv) The member libraries should be willing partners, ready to buy hardware, etc. and should be willing to send professional staff for training. They should be willing to pool bibliographic records to the Central Host of the network besides adhering to other network obligations.
(xv) A performance criterion should be developed and agreed upon to evaluate the working of the network.
2.5.1 Hardware and Software Requirements
(a) Hardware Requirements
Each of the member libraries must have at least some of the following hardware. However, the main library (Central Host) may require most of the hardware mentioned below, but with additional disk space. Hardware specifications are given below:
I. Server :
- Pentium @233 MHz with 64 MB RAM
- 1.2 GB HDD
- 32 x CDROM Drive
- 1.44" Floppy Drive
- Color Monitor (SVGA)
- Windows-NT Operating System
- MS-SQL Server 6.5
II. Client :
- Pentium @233 MHz with 32 MB RAM
- 1.2 GB HDD
- 1.44" Floppy Drive
- Colour Monitor (SVGA)
- Windows-98 Operating System
III. Other Hardware
- Fax (with dedicated phone line)
- Modem (with dedicated phone line)
- Telex
- CD-ROM drive
- At least two determine printers
- One letter quality printer (preferably laser printer)
- Cartridge type drive
(b) Software Requirements
Each of the participating libraries must have the following:
- Software for effective network operation as well as the library automation
- DOS (latest version) and/or
- UNIX (latest version, to begin with, it may be optional)
- LAN (Novel/Ethernet, to begin with, it may be optional)
- Software for E-mail (at least PROCOMM)
- Word processors
- DBMS packages
- IR packages CDS/ISIS
- Library automation : Libsys/Granthalaya/any other similar packages
- Programming languages : C/C++
(c) Software Evaluation
Software evaluation is quite often a difficult task. We have to consider the following procedure, criteria and features to evaluate software packages.
c.1 Procedures for Evaluation
The following procedures may be considered to evaluate software packages:
- Select a software after carefully examining the existing literature
- Examine carefully its literature and documentation
- Compare it with various other packages, keeping in view the following points
- Is it easy to understand?
- Is a separate training required?
- Is it menu driven?
- Can it handle records of variable sizes?
- Is it easy to edit a record?
- Is it difficult to update the files (inserting or deleting records?)?
- How much memory and hard disk space are required?
- On-site evaluation
- Post installation service (if the software is corrupted for various reasons, will the vendor replace it?
c.2 Criteria for Evaluation
Some of the criteria for evaluation of software are::
- Ease of operation
- Quality of documentation
- Hardware limitations
- Speed of operation
- Security in multi-user environment
- De-bugging facility and proper error messages while executing
- Support from vendor
c.3 Features of Software
Some of the important features of software are:
- User friendly
- Provision to on-line interaction, especially while editing inputting, retrieving and in data management.
- Provision to obtain outputs in various formats
- Compatibility and portability.
(d) Factors to be considered
Finally, one has to consider several factors while acquiring a computer. These are:
- memory size
- auxiliary storage devices like tape, disk, cassette, etc.
- availability of terminal
- speed and capabilities of input and output devices such as the ability to process lower case letters and special symbols.
- other machines especially with locally available machines
-with main frame computers, which may be available in the parent organization
- availability of computer for popular languages
- capabilities of operating system
- availability of special purpose software are
Therefore, we should take into account various specifications regarding establishment of a Library Network. The objectives, functions, requirements for hardware and software and structure of the network should be pre-defined before the establishment of a library network.